
| Network Security Overview |
| Product: | Strategi - BusinessLink/WEB | |
| Modified Date: |
|
Introduction
Individuals and corporations are implementing the Intranet/Extranet model for network communications at an alarming rate. Intranets and Extranets offer clear cost savings and ease of installation compared with older, more expensive leased line networks or WANS based on proprietary technology. Organizations can use Intranets and Extranets to distribute information more cost effectively and in a more timely manner. And, they can use them to improve collaboration among employees across the organization and with business partners. As Intranets and Extranets are becoming more widely deployed, new security challenges have emerged. While many organizations have deployed firewalls and access control technology to improve security, these technologies leave many security issues unaddressed. This overview will illustrate the main security risks of deploying Intranets and Extranets and how BusinessLink/WEB and Strategi work to resolve these issues. Goals of Security Systems Secure Sockets Layer (SSL) Digital Certificates Common Security Technologies BusinessLink Security Options Question and Answer Useful Security Reference Sites |
|
Although most people have heard the term 'hacker' in the media, in reality, corporate insiders- such as employees, former employees, contractors working onsite and other suppliers- are far more likely to attack their own companies computer system over an Intranet or Extranet. The figure below associates the type of attack with average loss as reported by a CSI/FBI 1998 Survey of Computer Security. 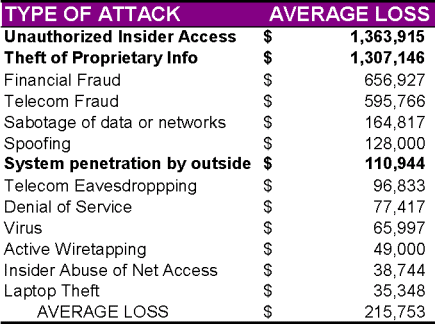
|
|
This last goal is frequently overlooked. Organizations must not only develop sound security measures, they must also find a way to ensure consistent compliance with them. If users find security measures cumbersome and time consuming to use, they are likely to find ways to circumvent them— thereby putting your Intranet and Extranet at risk. Organizations can ensure the consistent compliance to their security policy through: |
|
SSL is based on cryptography, the encoding of data in such a way that it can be decoded only by its intended recipient, not by a third party who might be able to intercept the information in transit. The simplest way to do this is for the sender and receiver to use a secret key, which can be used along with an agreed-upon algorithm to scramble the data in such a way that only someone with the key can unscramble it. The secret key acts much like a password. One of the most well-known secret key systems is the Data Encryption Standard (DES), developed by the U.S. National Security Agency. SSL uses a secret key system called RC4, developed by RSA, Inc, to encrypt its transfers. The use of a secret key implies that the participants in the conversation must have selected a key and communicated it among themselves in a secure manner. However, when establishing an Internet connection, there is usually no pre-arranged key, so a means must be provided of securely generating one. This would become a chicken-and-the-egg problem (how do you communicate a secret key with a secret key to encode it?) were it not for public key cryptosystems, of which RSA is the most used. A public key system, usually based on mathematical principles of modulo arithmetic, uses two keys, not one. Information encrypted with one of the keys can only be decrypted with the other key, and vice versa. You cannot encrypt and then decrypt a message with only one key - the result would be gibberish. Typically, one key is published (the public key) and the other is kept secret (the private key). Now anyone can encrypt a message using the public key and transmit it across an insecure network, knowing that only the holder of the private key can decrypt it. Not only can you encrypt with the public key, but you can also encrypt with the private key. Anyone can decrypt such a message, but only the private key holder could have generated it in the first place. This gives us a means of digitally signing messages in a way that no one else (without the private key) could duplicate. Thus, public key cryptosystems provide us with both confidentiality (no one can read a message but the receiver) and authenticity (no one can write a message but the sender). SSL operates using these principles. When an SSL session is established, the server begins by announcing a public key to the client. No encryption is in use initially, so both parties (and any eavesdropper) can read this key, but the client can now transmit information to the server in a way that no one else could decode. The client generates 46 bytes of random data, forms them into a single very large number according to PKCS#1, encrypts them with the server's public key, and sends the result to the server. Only the server, with its private key, can decode the information to determine the 46 original bytes. This shared secret is now used to generate a set of conventional RC4 keys to encrypt the rest of the session. The only issue that remains is authentication. How does the client know that the server is actually what it claims to be, and not some interlopper sending its own set of public keys? The answer is provided by certificates. A certificate is a cryptographically sealed data object that includes the server's identity and public key. The certificate is signed by computing its hash value and encrypting this with an issuer's private key. If even one bit is changed in the certificate, the hash value changes, and the signature becomes invalid. If the client already possesses the issuer's public key, and trusts the issuer to verify the identity of the server, then the client can be sure that the public key in the certificate is the public key of the server. An interlopper would have to know either the private key of the server or the private key of the issuer to successfully impersonate the server. As it turns out, only a handful of issuers are needed. For example, VeriSign, a major U.S. issuer, issues certificates only after a background check insures both the identity of the subject, and their authority over a particular DNS name. VeriSign's public keys are hardwired into both Netscape's and Microsoft's web browsers, so a server with a VeriSign-signed certificate can be authenticated by a browser with no additional information. If the server presents a certificate not signed by VeriSign (or another recognized authority), or if the DNS name of the server doesn't match the DNS name in the certificate, a warning message is displayed, and the user may decide how to proceed. The client can be authenticated as well, by presenting a certificate of its own, then computing a hash of all the SSL messages that have been exchanged up to a certain point, encrypting the result with its private key, and sending this to the server. The server, which can compute the same hash value, having seen all the messages as well, can decrypt using the client's public key, which is part of the certificate, and verify that the two results are the same. Thus the client is authenticated. |
|
Understanding digital certificates is central to understanding public key infrastructure systems. A digital certificate, also known as a Digital ID, is the electronic equivalent of a passport or business license. It is a credential, issued by a trusted authority, which individuals or organizations can present electronically to prove their identity or their right to access information. When a Certification Authority (CA) such as Thawte USA, issues Digital IDs, it verifies that the owner is not claiming a false identity. Just as when a government issues a passport, it is officially vouching for the identity of the holder, when a CA gives your business a digital certificate, it is putting its name behind your right to use your company name and Web address. How Digital Certificates Work In physical transactions, the challenges of identification, authentication, and privacy are solved with physical marks, such as seals or signatures. In electronic transactions, the equivalent of a seal must be coded into the information itself. By checking that the electronic "seal" is present and has not been broken, the recipient can confirm the identity of the message sender and ensure that the message content was not altered in transit. To create an electronic equivalent of physical security, digital certificates use advanced cryptography. Cryptographic systems have been used to protect valuable information for thousands of years. Traditionally, cryptographic systems have attempted to ensure security using some variant of the secret key system. Secret key systems require that both parties in a communication scheme have a copy of the same secret code or "key." When two people wanted to share information, the sender would encrypt the information using his copy of the secret key. The recipient could decrypt the message only by using her copy of the same key. If somebody intercepted the message, that person could not decipher it without the key. Despite their widespread use, secret key systems have several critical limitations. First, simply transmitting the secret key poses risks because the key can be intercepted in-transit by unauthorized parties. Second, if one of the sharing parties uses the key maliciously, that party can deny or repudiate, the transaction. Alternatively, the malicious party can impersonate the sender, or can use the secret key to decrypt other sensitive information. To prevent against this sort of attack, organizations must require users to have different secret keys for each party with whom they communicate. If an organization has a hundred people, literally millions of different secret keys will need to be used to accommodate all possible combinations. Digital certificates employ the more advanced public key cryptography system, which does not involve the sharing of secret keys. Rather than using the same key to both encrypt and decrypt data, a digital certificate uses a matched pair of keys that uniquely complement each other. When a message is encrypted by one key, only the complementary key can decrypt it. In public key cryptography systems, when your key-pair is generated, you keep one key private. This key is called the "private key," and nobody other than you, as the rightful owner, should ever have access to it. However, the matching "public key," can be freely distributed as part of a digital certificate. You can share your digital certificate with anyone, and can even publish your certificate in directories. If someone wants to communicate with you privately, they use the public key in your digital certificate to encrypt information before sending it to you. Only you can decrypt the information, because only you have your private key. The figure below illustrates the use of digital certificates.
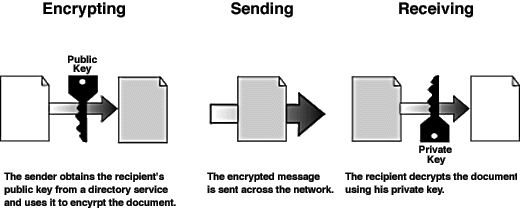
Conversely, you can use your key pair to digitally sign a message. To sign a message, you simply encrypt the message with your private key. The message can be decrypted using the public key contained within your certificate. While many people have access to your certificate, only you could have signed the message, because only you have access to your private key. A digital certificate is a binary file. Your digital certificate contains your name and your identifying information along with your public key-- it tells correspondents that your public key belongs to you. Digital certificates generally also contain a serial number, an expiration date, and information about the rights, uses, and privileges associated with the certificate. Finally, the digital certificate contains information about the certificate authority (CA) who issued the certificate. All certificates are digitally signed using the private key of the Certificate Authority. (Generally, the Certification Authorities’ own certificate (called a root certificate) is widely deployed in software packages, allowing people to seamlessly identify legitimate certificates issued by the certification authority.) If the CA maintains good security protection of their private key, it is virtually impossible for anyone to forge a digital certificate. It is important to note that certificates are not only issued to individuals. Organizations, as well as entities such as servers and routers, can also be issued certificates. Digital Certificates Meet Your Security Objectives Given the ease and versatility of PKI, security technology based on Digital Certificates has been deployed widely over the past several years. These widely used security protocols include:
|
|
Authenticode
CryptoAPI
Kerberos Authentication Protocol
Server Gated Cryptography
Smart Cards
Virtual Private Networks
Only two combinations of these protocols can be used to provide a secure VPN: |
|
BusinessLink/REMOTE
Security Options Security Summary
BusinessLink/WEB
Security Options Security Summary
Strategi
Security Options Security Summary |
|
Q: Why are passwords insufficient in some cases? A: Passwords can be subjected to brute-force attacks, cracked using common password databases, shared, stolen or inadventently surrendered to the wrong people. Q: How can SSL benefit my website? A: Aside from securing all client/server data transmissions, SSL enables the elimination of the paper trail associated with many administrative tasks. For example, users can submit required information through forms on secured websites which can be processed immediately upon receipt. Not only can the user be assured that their information is not intercepted and compromised, their requests can be processed much quicker than traditional means. Q: How can digital certificates benefit my website? A: Digital certificates can eliminate the need to maintain user name and password databases while proving the identity of the remote user. Q: How can I secure my email sent to other people? A: Personal digital certificates can be used to 'sign' the email message. When the email is received, the recipient must decrypt the email using the originator's public key. If the decryption of the email fails, the recipient know that the message has either been corrupted in transmit or not sent by the person who owns the public key used to decrypt the message. Using digital certificates with email ensures both sender identity and content integrity. Q: How can I secure my iSeries 400 from denial of service attacks? A: The most common method is using packet filtering on a firewall or router. Determine the services and ports (i.e. telnet, ftp, etc) that the iSeries 400 must provide and set up a packet filter on all ports that are not required. |
|
Cert Coordination Center At the CERT Coordination Center, they study Internet security vulnerabilities, provide incident response services to sites that have been the victims of attack, publish a variety of security alerts, research security and survivability in wide-area-networked computing, and develop information to help you improve security at your site. Verisign VeriSign, Inc., (NASDAQ: VRSN) is headquartered in Mountain View, CA and is the leading provider of Public Key Infrastructure (PKI) and digital certificate solutions used by enterprises, Web sites, and consumers to conduct secure communications and transactions over the Internet and private networks. RSA Founded in 1982 by the inventors of the RSA Public Key Cryptosystem (RSA is named after their surnames' first letters; Rivest, Shamir and Adleman.), RSA Data Security, Inc. is the world's brand name for cryptography, with more than 400 million copies of RSA encryption and authentication technologies installed and in use worldwide. Counterpane Counterpane Systems is a cryptography and computer security consulting firm. They are a virtual company based in Minneapolis, with four full-time employees and six part-time contractors. Counterpane provides expert consulting in design and analysis, implementation and testing, threat modeling, and export consulting to name a few. Microsoft Security Advisor The Microsoft security advisor site contains security information pertaining to Microsoft products as well as bulletins on new technologies and new discovery of potential security risks. ** End of Technical Support Bulletin ** |